Table of Contents
ToggleA. Details of Case Study/Project

In 2020, XYZ Security observed attackers pivoting their attacks to businesses for which global COVID-19 response efforts heavily relied, such as hospitals, medical and pharmaceutical manufacturers, as well as energy companies powering the COVID-19 supply chain.
“India was the second most attacked country in the Asia Pacific. Attacks on India made up 7 per cent of all attacks observed on Asia in 2020. “Finance and insurance were the top attacked industry in India (60 per cent), followed by manufacturing and professional services,” the report said.Ransomware was the top attack type, accounting for around 40 per cent of total cyber-attacks.
Banks need to assess their Cyber Security preparedness under the active guidance and oversight of the IT Sub Committee of the Board or the Bank’s Board directly. Also, the Banks need to report to Cyber Security and Information Technology Examination (CSITE) Cell of Department of Banking Supervision, Reserve Bank of India the following:
• identified gaps w.r.t. Cyber Security/Resilience Framework
• proposed measures/controls and their expected effectiveness
• milestones with timelines for implementing the proposed controls/measures and
• measurement criteria for assessing their effectiveness including the risk assessment and risk management methodology followed/proposed by the bank
The RBI has imposed, by an order dated November 30, 2018, a monetary penalty of Rs. 10 million on Indian Bank for contravention of circular on Cyber Security Framework in banks. To avoid this heavy penalty of contravention, the company wants to get reviewed their Cyber Security policies and procedures by professional IT audit firm to ensure that their policies and procedures on cyber security are in line with RBI Guidelines framework. To carry out review of their cyber security policies and procedures, board of directors of bank have hired XYZ and Associates.
B. Project Report
1. Introduction
ABC Bank Limited:
ABC Bank Limited incorporated in 1989, has its registered office in Mumbai, Maharashtra. Since its incorporation, it has come a long way in the banking industry. Currently, it offers a wide range of banking products and financial services for corporate and retail customers through a variety of delivery channels and specialized subsidiaries in the areas of investment banking, life, non-life insurance, venture capital and asset management.
The bank has a network of 2,500 branches and 10,000 ATMs across India and has presence in 10 countries, employing more than 50,000 employees.
AXYZ and Associates:
XYZ and Associates is an audit firm established in the year 2010. The firm has a standing of more than a decade in this profession. The firm specializes in information systems audit, enterprise risk management, designing and implementation of regulatory compliance framework and advisory. The firm has 3 partners, 5 articled assistants and 10 support staffs with its offices situated in Bangalore, Chennai and Delhi. Over the period of years, the firm has successfully handled IS audits of various banks, MNC’s and corporates.
The firm is represented by Ms. X as the team lead for Reviewing the Cyber Security Policies and Procedures.
The composition of the entire team is as under:
Ms. X
Qualification : FCA, DISA
Experience : 12 Years of Experience in IS Audit, ERP Audit and Central Bank Audit
Mr. Y
Qualification : FCA, DISA
Experience : 10 Years of Experience in IS Audit, Risk consultancy Services
Ms. Z
Qualification : FCA, DISA
Experience : 10+ years of experience in IS Audit, Implementation of Regulatory Compliance Framework
2. Auditee Environment
ABC Bank Limited (“The Company”) incorporated in 1989, has its registered office in Mumbai, Maharashtra. The bank offers a wide range of banking products and financial services for corporate and retail customers through a variety of delivery channels and specialized subsidiaries in the areas of investment banking, life, non-life insurance, venture capital and asset management.
The organization structure of the company:
On the technological front, the company has been a forerunner in many technological innovations in the banking industry such as Internet Banking, Mobile Banking and Fully Automated Touch Banking. The urge to innovate and improve customer satisfaction is never-ending where it came up recently with the facilities of contactless Debit and Credit Cards. Moreover, the bank has an advanced internet banking platform allowing customers to personalize their online banking experience, leaving no stone unturned in its futuristic approach.
The Company has documented policies and procedures for Accounting, Administration, Customer Services, Cyber Security Policy, Fair Disclosure Policy, Finance, Information Technology, Marketing, Preservation of Documents, and Whistle Blower Policy
3. Background
The Reserve Bank of India (RBI) has cautioned all the banks that in the post Covid-19 lockdown period, there has been increased incidence of cyber threats against the banking industry. The Central Bank underscored that the banking industry is the target of choice for cyber-attacks.
ABC Bank Limited greatly relies on information technology for its day-to-day functioning. Hence, as a preventive measure, the company wants to ensure that their policies and procedures on cyber security are effective and efficient to mitigate any potential risks. Mr. E, the Chief Technology Officer of the company has appointed XYZ and Associates to review their cyber security policies and procedures to identify any gaps in their processes and curb the same before any attacks.
4. Situation
ABC Bank Limited has a network of 2500 Branches and 10,000 ATMs across India and has a presence in 10 countries, employing more than 50,000 employees.
Currently it offers a wide range of banking product and financial services for corporate and retail customers through a variety of delivery channels and specialized subsidiaries in the areas of investment Banking, life, non-life insurance, venture capital and asset management.
Reserve Bank of India issued a comprehensive Circular on June 2, 2016, underlining the urgent need to put in place a robust cyber security/resilience framework at banks and to ensure adequate cyber security preparedness among banks on a continuous basis. The Reserve Bank of India (RBI) has cautioned that in the post Covid-19 lockdown period, there has been increased incidence of cyber threats against the banking industry.
With more people opting for digital transactions, hackers can easily hack into banking applications to steal the personal data of customers. Banking technology thus needs to be stringent and vigilant against cyber security threats.
5. Terms and Scope of assignment
Based on the understanding of the company’s need for conducting the review of Cyber Security policies and procedures, the primary focus of audit is directed towards the adequacy and appropriateness of the system and identification of any risks associated therein and also ensuring the confidentiality, integrity and availability of the data processed.
The detailed scope of review/consultation was decided in consultation with the Top Management and the Managing Director and Operations Director of the Company. The scope of review was from security/controls, and benefits realization perspective and involved the following:
1. An assessment of the degree to which cyber security access measures are applied in the Bank.
2. A review of the company’s infrastructure and technology architecture
3. A review of application/system development practices
4. A review of non-IT safeguards such as premises and facilities, information classification, and employee and contractor security screening
5. A review of security policy and procedures existing to protect the Information Systems infrastructure
6. A review of roles and responsibilities with regard to information risk that have been established by the Company with best practice guidelines
7. A review of processes for reporting and management of information security breaches
8. To help ensure password controls have been established that confirm to best practice and effective controls are in place
9. A review of the controls in place over the use of portable devices including USB’s and external hard disk drives
10. To undertake audit work into the secure use of email data devices, third party email accounts and any methods of data transfer.
6. Logistic arrangements required
The Company shall appoint one Senior IT Officer part of the implementation team, and operations head to co-ordinate for finalizing the initial work plan and shall continue to work with the audit team as and when required till the completion of assignment. The Bank shall make available necessary systems, software, software resources and support facilities for completing the assignment within the appointed time. During the course of audit, the following resources shall be made available:
• Computers/Laptops with internet access, Other Hardware like Printers.
• Scanners, Modems, Router, UPS, Hubs, Switches, LCD Projector, Storage Devices like Pen Drive/Hard Drive
• LAN connection
• Access to servers, workstations, financial applications and other application software used by the company
• Separate User ID and password for the audit team
• Adequate seating space for our audit team and safe storage facility for keeping papers
• Facilities for discussions amongst our team and company’s designated staff
• Access to SLA between vendor and Auditee
• Access to all errors/exception’s reports
• Access to all testing documentations and checklists.
• Access to recent audit reports.
• Access to all the policies and documentations related to cyber securities
• Soft copy of log generated by system
• Travelling facility locally and for outstation.
7. Methodology and Strategy adapted for execution of assignment
Prescribed guidelines:
The company is covered under level II as per RBI circular DoS.CO/CSITE/BC.4083/31.01.052/2019-20. In addition to level I controls, the additional controls include Data Loss Prevention Strategy, Anti-Phishing, VA/PT of critical applications. The review is based on the framework and guidelines of RBI.
Methodology:
The strategy for review would be as demonstrated below:
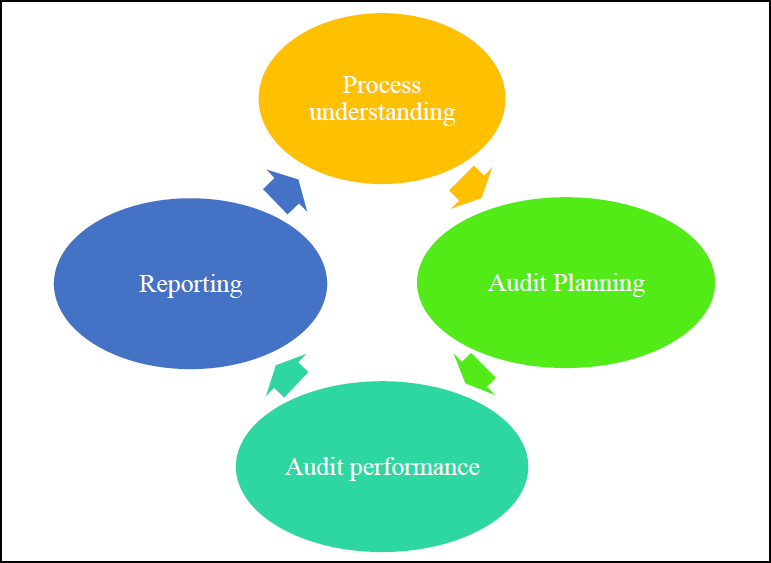
• Obtaining an understanding of the Company’s most important information technology assets
• Identifying what data breach would have a major impact on the business whether from malware, cyber-attack or human error
• Identifying the internal and external vulnerabilities
• Assessing impact if those vulnerabilities are exploited
• Obtaining an understanding of the level of risk the Company is comfortable taking.
Cyber Security Policy Framework
“• Whether the policy defines and adopts a comprehensive Cyber Security Framework that includes:
– Cyber Security Strategy
– Cyber Security Policy & Procedures
– Assessment of cyber threats and risks
Whether the controls are implemented as defined in the guidelines for Cyber Security framework”
Cyber Security Policy to be distinct from the IT policy/IS Policy
“• Whether the Cyber Security Policy is distinct from the IT/IS policy so that it highlights the risks from cyber threats and the measures to address/reduce these risks
• While identifying and assessing the inherent risks, the bank should keep in view the technologies adopted, delivery channels, digital products being offered, internal and external threats etc., and rate each of these risks as Low, Medium, High and Very High”
IT Architecture/Framework should be security compliant
“• The IT architecture/ framework which includes network, server, database and application, end user systems, etc., should take care of security measures at all times and this should be reviewed by the Board or IT Sub-committee of the Board periodically
To ensure the same, the following steps are carried out: • Identify weak/vulnerable areas in IT systems and processes • Check whether restricted access is allowed to networks, databases and applications wherever permitted, through well-defined processes and approvals including rationale for permitting such access • Assess the cost of impact in case of breaches/failures in these areas and review whether a suitable Cyber Security System is put in place to address them”
Cyber Crisis Management Plan
“• Review whether the Cyber Crisis Management Plan (CCMP) is based on:
– National Cyber Crisis Management Plan (CERT-IN)
– Cyber Security Assessment Framework (CERT-IN)
– CERT-In/NCIIPC/RBI/IDRBT guidance
• Review BCP/DR program and whether the same aligns with Cyber Crisis Management Plan (CCMP).
• Whether preventive, detective, and corrective controls are in place to protect Bank against cyber-threats, and to promptly detect, respond, contain, and recover from any cyber-intrusions.”
Organisational Arrangements
• Review the organisational arrangements so that the security concerns are brought to the notice of suitable/concerned officials to enable quick action.
Cyber Security awareness among Top Management/Board/other concerned parties
• Whether cyber security objectives are promoted among their customers, vendors, service providers and other concerned parties
Ensuring protection of customer information
• Whether appropriate steps in preserving the Confidentiality, Integrity and Availability of data is stored/in transit within themselves or with the third-party vendors is ensured
Supervisory reporting framework
• Whether the information security incident monitoring and management processes includes cyber security incidents and attempts
Apart from the above, the major areas of review would also include
i. Bank specific email domains (example, XYZ bank with mail domain xyz.in) with anti-phishing and anti-malware, DMARC controls enforced at the email solution.
ii. Two factor authentications for accessing their CBS and applications connecting to the CBS with the 2nd factor being dynamic in nature.
iii. Conduct security review of PCs/terminals used for accessing corporate Internet Banking applications, CBS servers and network perimeter through a qualified information security auditor.
iv. Password management policy
v. Anti-phishing campaigns
vi. Vendor/Outsourcing Risk Management
vii. Network Management and Security
viii. Secure Configuration
ix. Application Security Life Cycle (ASLC)
x. Change Management
xi. User Access Control / Management
xii. Authentication Framework for Customers
xiii. Data Leak Prevention Strategy xiv. Audit Logs
xv. Incident Response and Management
8. Documents reviewed
Below is a list of documents to review to complete the assignment.
1. Cyber Risk Management & Oversight
A. Organization chart
B. Cybersecurity related policies and procedures
C. Board/IT Committee minutes
D. Strategic plans
E. Employee incentive plans
F. Cybersecurity job descriptions
G. Cybersecurity personnel qualifications
H. Risk assessments
I. IT Audit schedule
J. Engagement letters
K. IT Audit reports and correspondence (includes financial audit if there were IT or cybersecurity scope areas)
L. Audit exception tracking (with emphasis on IT/Cybersecurity audits)
M. Risk management reports
N. Documentation evidencing employees have completed cybersecurity training and awareness training
O. Cybersecurity training policies and procedures.
P. Cybersecurity training and awareness materials
2. Cybersecurity Controls
A. List of physical access controls (such as key cards, biometric controls, video cameras)
B. Baseline security configuration standards
C. Software Development Life Cycle (SDLC)
D. Vulnerability/patch management policies and procedures
E. Patch management reports
F. Penetration test results/reports
G. Vulnerability assessments
3. External Dependency Management
A. List of third parties and subcontractors
B. Contracts governing all third-party relationships.
C. Inventory of all third-party connections, including connections to:
i. Customers,
ii. Third-party service providers,
iii. Business partners, and
iv. Other Internet connections (e.g., web server, remote maintenance, etc.)
D. Network topology/diagram
E. Independent reports on the service provider’s security controls
F. Remote access logs
G. Third-party employee access reviews
H. Vendor Management policies and procedures
4. Threat Intelligence and Collaboration
A. List of threat intelligence resources (e.g. industry groups, consortiums, threat and vulnerability reporting services)
B. Management reports on cyber intelligence
5. Cyber Resilience
A. Cybersecurity event log and reports on cyber incidents
B. Business Impact Analysis
C. Business/Corporate Continuity Plan
D. Results of resilience testing
E. Resilience testing reports
F. Cyber incident response plans
G. Crisis management plans
9. References
• RBI Circular DCBS.CO.PCB.Cir.No.1/18.01.000/2018-19 dated October 19, 2018 on Basic Cyber Security Framework for Primary (Urban) Cooperative Banks (UCBs) • RBI circular DoS.CO/CSITE/BC.4083/31.01.052/2019-20 dated December 31, 2019 on Comprehensive Cyber Security Framework for Primary (Urban) Cooperative Banks (UCBs) – A Graded Approach
• https://rbidocs.rbi.org.in
• https://www2.deloitte.com
• https://iu.instructure.com
• https://www.utah.gov
10. Deliverables
The report on Review of Cyber Security Policies and Procedures of ABC Bank Limited is to be furnished to appointing authority in prescribed manner after all findings and deficiencies were considered.
• Draft Report including executive summary of the result of the review along with the recommendations of findings and recommendations with risk analysis of findings
• Final Report incorporating Management Comments and agreed priority plan of action based on exposure analysis
• Soft Copy of Checklist used for the audit
• Soft Copy of Audit Methodology and documentation
11. Format of Report/ Findings and Recommendations
Issue: Physical access controls
Risk Rating: High
Audit Finding: During the review, we observed that although access to data centers and server room is restricted through biometric and ID access, there isn’t any screening of baggage/employees. There is no control restricting taking mobile phones, pen drives, cameras, etc. inside these premises.
Recommendations: Deploy security personnel who screens people accessing data centers and server room.
Management response: Noted for compliance
Issue: E-Mail protection
Risk Rating: Very High
Audit Finding: During review, it was observed that sensitive information and confidential documents can be emailed to outsiders, which can be accessed by the recipient without any authentication.
Recommendations: The policy should provide for authentication of the recipient of the email which contains confidential information.
Management response: Noted for compliance
Issue: Confidentiality marking
Risk Rating: High
Audit Finding: During the review, it was observed that while most of the documents and files were marked for confidentiality encryption, few file types such as PDF’s, images, containing important blueprints and data do not have the facility to mark for confidentiality.
Recommendations: The management has to update the file protection software to include encryption facility for all document types
Management response: Noted for compliance
Issue: Logical controls
Risk Rating: Medium
Audit Finding: Storage media if disposed without taking adequate precautions could result in disclosure of confidential or personal information.
All computers meant for sale/discard are kept in IT room. Hard disks of such computers are removed and stored separately. Hard disks are not
sold/discarded with the computer. There is no plan to destroy hard disk.
There is no documented process for media disposal.”
Recommendations: Procedure for destroying the data in the Hard Disks should be made.
Management response: Noted for compliance
Issue: System updates
Risk Rating: High
Audit Finding: Inadequate protection of all systems from viruses and Spyware may compromise systems/networks.
It was observed that the laptops used by agency staff/non-payroll staff which are connected to the company network is not covered in the push updates of security software.
The software updates of these systems are taken care by the respective companies where there are gaps in the security software updates”
Recommendations: The policy should provide for system updates of laptops/desktops used by agency staffs/non-payroll staff if they are connected to the company’s network or work with the vendor to include for software updates on regular basis in line with the company’s schedule
Management response: Noted for compliance
Issue: Noted for compliance
Risk Rating: Medium
Audit Finding: Absence of logging and review procedures for the servers may lead to an unauthorized activity going unnoticed with respect to financial data.
It was observed that though there were logs of key accesses and activities, there is no regular monitoring of the same by a person of substantial authority.
Currently monitored only by the IT personnel in case of any red flags
On sample verification of employee logs, it was observed that there was mismatch in the number of entries and exits, which indicates there were piggybacking.”
Recommendations: There should be regular monitoring of logs to key activities and accesses
Any red flags should be reported to a senior level management apart from the IT personnel
Employees should be strictly informed about the consequences of piggybacking
Locking of ID cards where there is double entry without exit.
Management response: Noted for compliance
Issue: Phishing
Simulations”
Risk Rating: Medium
Audit Finding: We found that the results of phishing simulations are neither reported to the respective departments nor to the management. The percentage of number of employees who have clicked on phishing mails are on the increasing trend since last year.
Recommendations: Reports of phishing simulations should be sent to respective departments and responsibility fixed.
Awareness programs highlighting the importance of IT security needs to be carried out
Management response: Noted for compliance
Issue: Cyber insurance
Risk Rating: Medium
Audit Finding: The company has not taken cyber insurance.
Recommendations: It is highly recommended to take cyber insurance to financially protect the company in the event of any data breach
Management response: Noted for compliance
Issue: Outsourcing cloud computing
Risk Rating: Medium
Audit Finding: The company has outsourced non-core banking activities to third part cloud computing.
The agreement provides for obtaining annual IS audit reports of such vendors.
On review, it was observed that such IS audit reports were not obtained.
Recommendations: It is very important for the 3rd party vendors to be subject to IS audit when they store banking information. The reports should be obtained and reviewed periodically to monitor any non-compliances
Management response: Noted for compliance
Issue: Restriction in number of requests
Risk Rating: Very High
Audit Finding: It was observed that few ATMs allow for unlimited number of fund withdrawals due to software issues. This poses serious threat of fraudulent transactions.
Recommendations: ATMs should be regularly updated and maintained for proper use.
Non-functional ATMs need to be closed.”
Management response: Noted for compliance
12. Summary/Conclusion
During the review of Cyber Security Policies and Procedures of ABC Bank Limited, we noted that the Cyber Security Policy that is followed by the Company is not updated and there were several instances of possibilities of threat / breach. Findings, recommendations and response from the Management thus provided in the Report to curb the gaps and secure the Company from cyber-attack.
Increase in the dependencies on system especially at this point of time due to COVID-19 where time is minutely crucial for both businesses and common man, cannot tolerate the risk of system downtime due to any probable attack. The Management is thus requested to provide adequate importance to the recommendations mentioned by the Review Team in order to mitigate the loss of time / data / money / reputation.
A similar review can be conducted at regular intervals of time which can help in immediately identifying the gap, and thereby mitigating the risk of loss as and when required. The Management is also requested to focus on the trainings to be provided to the employees on the awareness of cyber-attacks, along with improvement in Physical Access Controls as mentioned which is quite essential for the adequate security from the attacks towards the Company.
DISA 3.0 Project Report on:
1. IS Audit of Banking Application
2. Migrating to cloud based ERP solution
3. Security control review of railway reservation system
4. Security and control risk assessment of toll bridge operations
5. System audit of a hospital automation system
6. Review of vendor proposal for SaaS services
7. Information Systems audit of a mutual fund systems
8. Audit of outsourced software development
9. Network security audit of remote operations including WFH
10. Infrastructure audit of a Bank data Centre
11. Conducting vulnerability assessment and penetration testing
12. Auditing Business continuity plan for Manufacturing system
13. Assessing risk and formulating policy for mobile computing
14. Auditing robotic process automation system
15. Implementation of adequate governance in hotel management system
16. Outsourced migration audit of merger of Banks
17. Audit of an E-Commerce web site
18. Audit of Online booking system for a hotel chain
19. Audit of Business Continuity Planning of a financial institution
20. Audit of online brokerage firm
21. Audit of Security Operation Centre of a Bank
22. Audit of Cyber Security Framework of a PSB
23. EVALUATION OF OUTSOURCING IT OPERATIONS
24. Auditing SWIFT operations in a Bank
25. Project Report Template and Guidelines on Project Report Submission
26. Information Systems Audit of ERP Software
27 .Implementing Grc As Per Clause 49 Listing Requirements
28. Review of IT Security Policies and Procedures in audit
ISA 3.0 Video Lectures & Question Bank
₹6,165.00
Limited Time Offer get 40% discount
Coupon “rajat40”
Courses Included




Information Systems Audit (ISA 3.0) – Video Lectures & Question Bank
