0
Features Detailed explanation with my comments After submitting the quiz – Sort all wrong answers Increase your analytical skill. …
(
ratings )
2023
students
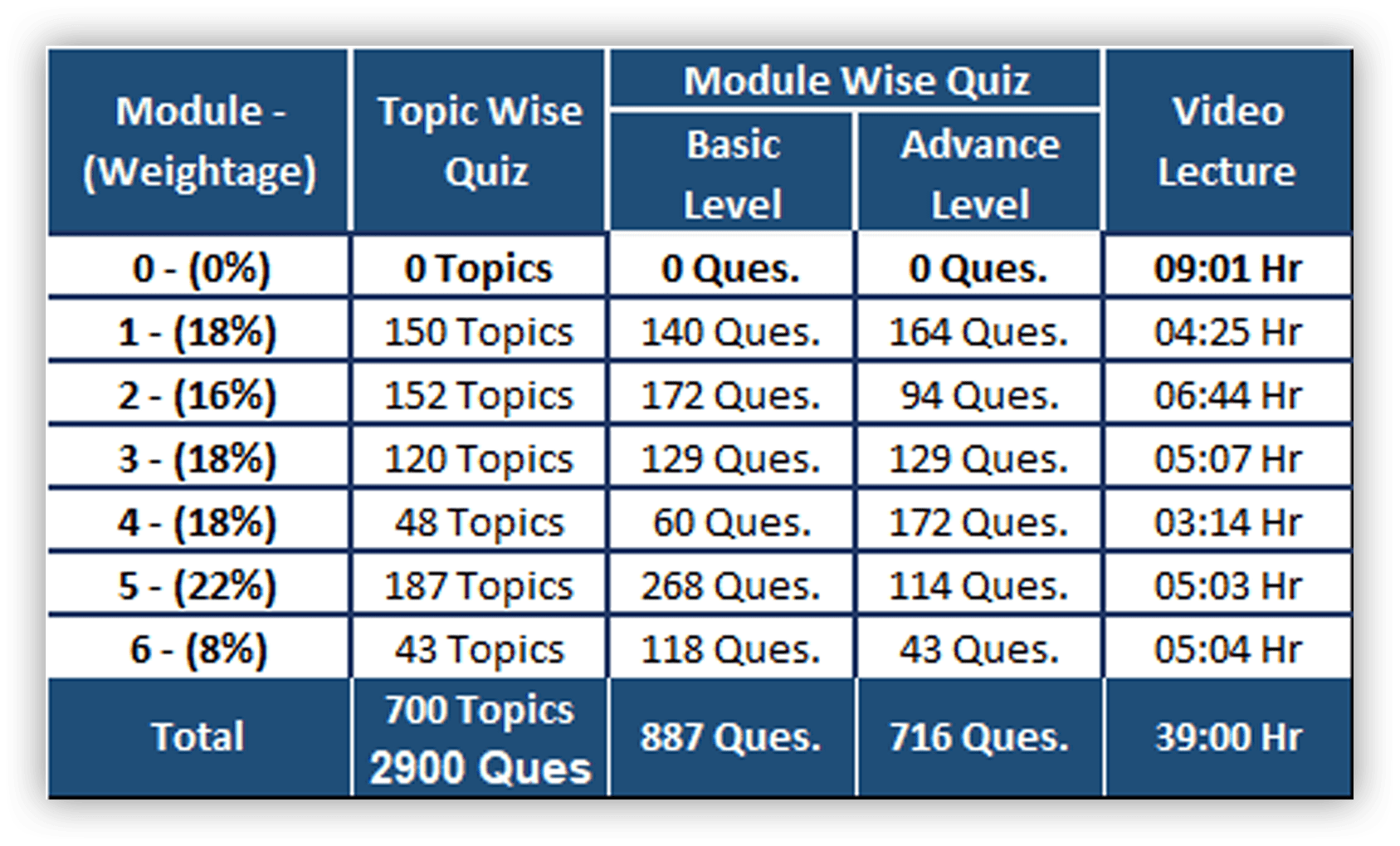
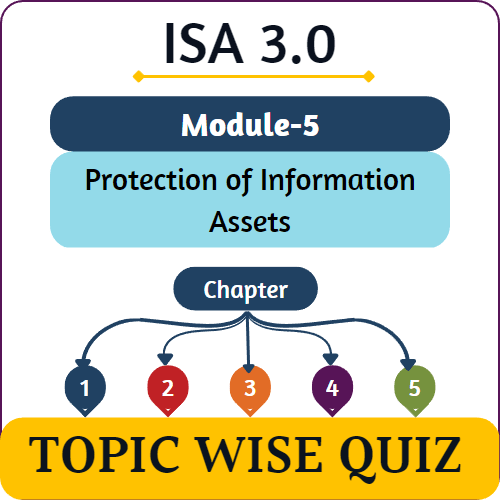
Features
- Detailed explanation with my comments
- After submitting the quiz - Sort all wrong answers
- Increase your analytical skill.
- You can retake quizzes multiple times.
- Practice Topic-wise quiz after every Chapter lecture.
- Each Module-wise quiz is divided into 2 sections
- basic & advance quiz (MTP)
- Save the quiz in between & continue solving anytime.
- Full mock tests in last week in exam conditions.
- Track your progress with instant evaluation.
- Get a Brief Overview of each topic in colourful charts.
Created by
19/06/2023
6 months
Course Currilcum
-
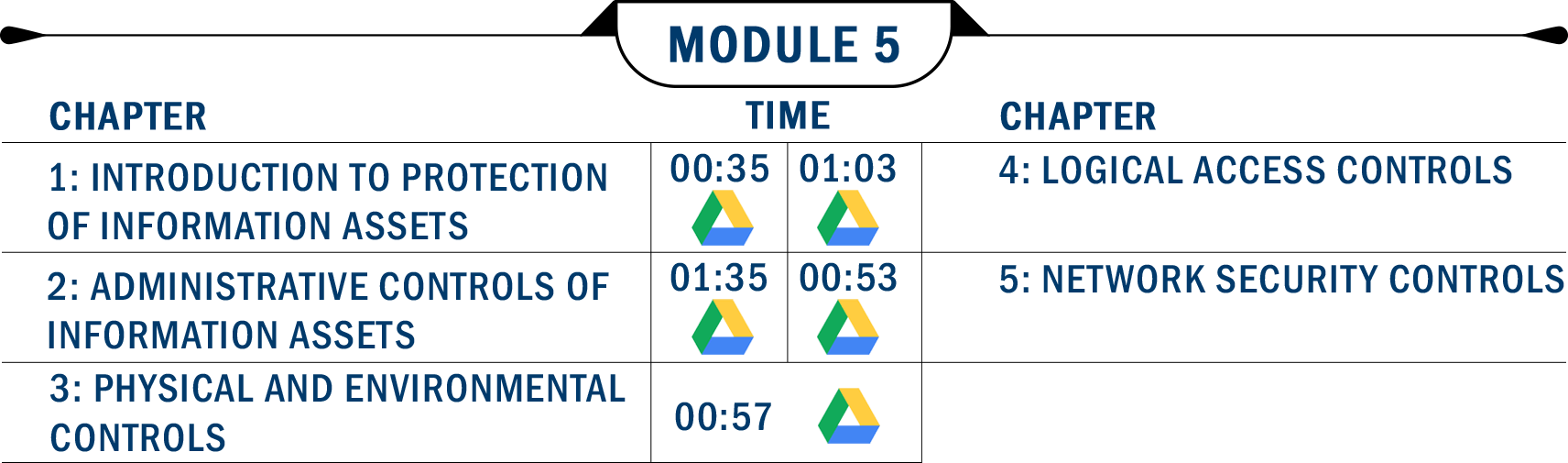
- Introduction to Protection of Information Assets Unlimited
- Risk Response-5 Unlimited
- Cyber Computer Attacks Unlimited
- Need for IS Controls Unlimited
- Types of Controls Unlimited
- Deterrent Control Unlimited
- Preventive Controls Unlimited
- Detective Controls Unlimited
- Corrective Controls Unlimited
- Periodic Review and Monitoring of Risk and Controls Unlimited
- Control Self Assessment Unlimited
- Role of IS Auditor in Information Risk Management Unlimited
-
- Administrative Controls of Information Assets Unlimited
- Information Security Management Unlimited
- Critical Success Factors to Information Security Management Unlimited
- Administrative Controls of Information Assets – Segregation of Duties Unlimited
- Rotation of Duties Unlimited
- Other Common Security Policies Unlimited
- Benefits from Classifications Unlimited
- Classification Schema Unlimited
- Administrative Controls of Information Assets – Training and Education Unlimited
- Issues and Challenges of Information Security Management Unlimited
-
- Physical and Environmental Controls Unlimited
- Sources of Physical Security Threats Unlimited
- Choosing and Designing a Secure Site Unlimited
- Security Management Unlimited
- Human Resource Controls Unlimited
- Perimeter Security Unlimited
- Smart Cards Unlimited
- Auditing Physical Security Controls Unlimited
- Objectives of Environmental Controls Unlimited
- Environmental Threats and Exposures Unlimited
- Environmental Control Techniques Unlimited
- Choosing and Designing a Safe Site Unlimited
- Facilities Planning Unlimited
- Maintenance Plan Unlimited
- Power Supplies Unlimited
- Fire Detection and Suppression Unlimited
-
- Logical Access Controls Unlimited
- Paths of Logical Access Controls Unlimited
- Logical Access Attacks and Exposures Unlimited
- Access Control Mechanisms Unlimited
- Identification Techniques Unlimited
- Authentication Techniques Unlimited
- Logical Access Controls – Passphrase Unlimited
- Token Based Authentication Unlimited
- Biometric Authentication – Biometric Unlimited
- Biometric Authentication – Equal-Error Rate. Unlimited
- Biometric Authentication – False Acceptance Rate Unlimited
- Biometric Authentication – Iris Scan Unlimited
- Authorization Techniques Operating System Unlimited
- Logical Access Policy & Procedures Unlimited
- Password Management Unlimited
- Network Access Controls Unlimited
- Application Access Controls Unlimited
- Operating System Access Controls Unlimited
- Identity and Access Management Unlimited
- Single Sign on Unlimited
- Access Controls in Operating Systems Unlimited
- Auditing Logical Access Controls Unlimited
-
- Network Security Controls Unlimited
- Network Threats and Attacks Unlimited
- Network Threats and Attacks – Botnets Unlimited
- Network Threats and Attacks – Cookies Unlimited
- Network Threats and Attacks – Ddos Unlimited
- Network Threats and Attacks – Denial-Of-Service Unlimited
- Network Threats and Attacks – Eavesdropping Unlimited
- Network Threats and Attacks – Impersonation Unlimited
- Network Threats and Attacks – Malware Unlimited
- Network Threats and Attacks – Ping Of Death Unlimited
- Network Threats and Attacks – Port Scan Unlimited
- Network Threats and Attacks – Reconnaissance Unlimited
- Network Threats and Attacks – Scripts Unlimited
- Network Threats and Attacks – Session Hijacking Unlimited
- Network Threats and Attacks – Spoofing Unlimited
- Network Threats and Attacks – Traffic Analysis Unlimited
- Network Threats and Attacks – Web Defacement Unlimited
- Network Threats and Attacks – Wireless: Unlimited
- Current Trends in Attacks Unlimited
- Network Security Control Mechanisms Unlimited
- Cryptography Unlimited
- Cryptography – Digital Certificate. Unlimited
- Cryptography – Cryptanalysis Unlimited
- Cryptography – Hashing Algorithms Unlimited
- Cryptography – Segmentation Unlimited
- Cryptography – Smime Unlimited
- Cryptography – Transport Layer Security Unlimited
- Cryptography – Transport Mode Unlimited
- Cryptography – Tunnel Mode Unlimited
- Types of Cryptography Unlimited
- Types of Cryptography – Authentication Unlimited
- Types of Cryptography – Symmetric Unlimited
- Public Key Infrastructure (PKI) Unlimited
- Public Key Infrastructure (PKI) – Digital Certificate. Unlimited
- Public Key Infrastructure (PKI) – Digital Signature Unlimited
- Public Key Infrastructure (PKI) – Pki Unlimited
- Public Key Infrastructure (PKI) – Private Key Unlimited
- Public Key Infrastructure (PKI) – Public Key Unlimited
- Public Key Infrastructure (PKI) – Public Key Infrastructure Unlimited
- Application of Cryptographic Systems Unlimited
- Application of Cryptographic Systems – Ipsec Unlimited
- Application of Cryptographic Systems – Secure Shell Unlimited
- Application of Cryptographic Systems – Secure Socket Layer Unlimited
- Application of Cryptographic Systems – Vpn Unlimited
- Remote Access Controls Unlimited
- Malicious Codes Unlimited
- Malicious Codes – Logic Bomb Unlimited
- Malicious Codes – Macro Virus Unlimited
- Malicious Codes – Master Boot Record (Mbr) Viruses: Unlimited
- Malicious Codes – Polymorphic Virus Unlimited
- Malicious Codes – Trojan Horse Unlimited
- Malicious Codes – Virus Unlimited
- Firewall Unlimited
- Intrusion Detection System – IPs Unlimited
- Intrusion Detection System – Ids Unlimited
- Intrusion Detection System – Intrusion Detection Unlimited
- Intrusion Detection System – Mac Address Unlimited
- Wireless Security Control Mechanisms Unlimited
- Wireless Security Control Mechanisms – Honeypot Unlimited
- Wireless Security Control Mechanisms – Mac Address Unlimited
- Wireless Security Control Mechanisms – Man-In-The-Middle Unlimited
- Wireless Security Control Mechanisms – Wireless: Unlimited
- VOIP Security Controls Unlimited
- Vulnerability Assessment and Penetration Testing Unlimited
- Vulnerability Assessment and Penetration Testing – Penetration Testing Unlimited
- Vulnerability Assessment and Penetration Testing – Social Engineering Unlimited
- Vulnerability Assessment and Penetration Testing – War Dialing Unlimited
- Vulnerability Assessment and Penetration Testing – Wireless: Unlimited
- Auditing Network Security Controls Unlimited